Сейчас 127 заметки.
Установка/настройка хостинг панели ISPConfig 3 на Debian: различия между версиями
м (Правки 94.242.255.188 (обсуждение) откачены к версии Adkrasyuk) |
Znayka (обсуждение | вклад) |
| (не показаны 4 промежуточные версии 3 участников) | |
(нет различий)
| |
Текущая версия на 21:36, 2 июля 2015
1. Install The SSH Server[править]
If you didn't install an SSH server during the basic system installation, you can do it now:
apt-get install ssh openssh-server
From now on you can use an SSH client such as PuTTY and connect from your workstation to your Debian Squeeze server and follow the remaining steps from this tutorial
2. Install vim-nox (Optional)[править]
I'll use vi as my text editor in this tutorial. The default vi program has some strange behaviour on Debian and Ubuntu; to fix this, we install vim-nox
apt-get install vim-nox
(You don't have to do this if you use a different text editor such as joe or nano.)
3. Configure The Network[править]
Because the Debian Squeeze installer has configured our system to get its network settings via DHCP, we have to change that now because a server should have a static IP address. Edit /etc/network/interfaces and adjust it to your needs (in this example setup I will use the IP address 192.168.0.100) (please note that I replace allow-hotplug eth0 with auto eth0; otherwise restarting the network doesn't work, and we'd have to reboot the whole system):
vi /etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
#allow-hotplug eth0
#iface eth0 inet dhcp
auto eth0
iface eth0 inet static
address 192.168.0.100
netmask 255.255.255.0
network 192.168.0.0
broadcast 192.168.0.255
gateway 192.168.0.1
Then restart your network:
/etc/init.d/networking restart
Then edit /etc/hosts. Make it look like this:
vi /etc/hosts
127.0.0.1 localhost.localdomain localhost 192.168.0.100 server1.example.com server1 # The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters
Now run
echo server1.example.com > /etc/hostname
/etc/init.d/hostname.sh start
Afterwards, run
hostname
hostname -f
It is important that both show server1.example.com now!
4. Update Your Debian Installation[править]
First make sure that your /etc/apt/sources.list contains the squeeze-updates repository (this makes sure you always get the newest updates for the ClamAV virus scanner - this project publishes releases very often, and sometimes old versions stop working)
vi /etc/apt/sources.list
[...] deb http://ftp.de.debian.org/debian/ squeeze-updates main [...]
Run
apt-get update
to update the apt package database and
apt-get upgrade
to install the latest updates (if there are any).
5. Change The Default Shell[править]
/bin/sh is a symlink to /bin/dash, however we need /bin/bash, not /bin/dash. Therefore we do this:
dpkg-reconfigure dash
Use dash as the default system shell (/bin/sh)? <-- No
6. Synchronize the System Clock[править]
It is a good idea to synchronize the system clock with an NTP (network time protocol) server over the Internet. Simply run
apt-get install ntp ntpdate
and your system time will always be in sync.
7. Install Postfix, Dovecot, Saslauthd, MySQL, phpMyAdmin, rkhunter, binutils[править]
We can install Postfix, Dovecot, Saslauthd, MySQL, phpMyAdmin, rkhunter, and binutils with a single command:
apt-get install postfix postfix-mysql postfix-doc mysql-client mysql-server openssl getmail4 rkhunter binutils dovecot-imapd dovecot-pop3d sudo
You will be asked the following questions:
General type of mail configuration: <-- Internet Site System mail name: <-- server1.example.com New password for the MySQL "root" user: <-- yourrootsqlpassword Repeat password for the MySQL "root" user: <-- yourrootsqlpassword
Next open the TLS/SSL and submission ports in Postfix:
vi /etc/postfix/master.cf
Uncomment the submission and smtps sections (leave -o milter_macro_daemon_name=ORIGINATING as we don't need it):
[...] submission inet n - - - - smtpd -o syslog_name=postfix/submission -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes -o smtpd_client_restrictions=permit_sasl_authenticated,reject # -o milter_macro_daemon_name=ORIGINATING smtps inet n - - - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes -o smtpd_client_restrictions=permit_sasl_authenticated,reject # -o milter_macro_daemon_name=ORIGINATING [...]
Restart Postfix afterwards:
/etc/init.d/postfix restart
We want MySQL to listen on all interfaces, not just localhost, therefore we edit
/etc/mysql/my.cnf and comment out the line bind-address = 127.0.0.1:
vi /etc/mysql/my.cnf
[...] # Instead of skip-networking the default is now to listen only on # localhost which is more compatible and is not less secure. #bind-address = 127.0.0.1 [...]
Then we restart MySQL:
/etc/init.d/mysql restart
Now check that networking is enabled. Run
netstat -tap | grep mysql
The output should look like this:
root@server1:~# netstat -tap | grep mysql tcp 0 0 *:mysql *:* LISTEN 10617/mysqld root@server1:~#
8. Install Amavisd-new, SpamAssassin, And Clamav[править]
To install amavisd-new, SpamAssassin, and ClamAV, we run
apt-get install amavisd-new spamassassin clamav clamav-daemon zoo unzip bzip2 arj nomarch lzop cabextract apt-listchanges libnet-ldap-perl libauthen-sasl-perl clamav-docs daemon libio-string-perl libio-socket-ssl-perl libnet-ident-perl zip libnet-dns-perl
The ISPConfig 3 setup uses amavisd which loads the SpamAssassin filter library internally, so we can stop SpamAssassin to free up some RAM:
/etc/init.d/spamassassin stop
update-rc.d -f spamassassin remove
9. Install Apache2, PHP5, phpMyAdmin, FCGI, suExec, Pear, And mcrypt[править]
Apache2, PHP5, phpMyAdmin, FCGI, suExec, Pear, and mcrypt can be installed as follows:
apt-get install apache2 apache2.2-common apache2-doc apache2-mpm-prefork apache2-utils libexpat1 ssl-cert libapache2-mod-php5 php5 php5-common php5-gd php5-mysql php5-imap phpmyadmin php5-cli php5-cgi libapache2-mod-fcgid apache2- suexec php-pear php-auth php5-curl php5-mcrypt mcrypt php5-imagick imagemagick libapache2-mod-suphp libruby libapache2-mod-ruby libapache2-mod-python libapache2- mod-perl2
You will see the following questions:
Web server to reconfigure automatically: <-- apache2 Configure database for phpmyadmin with dbconfig-common? <-- No
Then run the following command to enable the Apache modules suexec, rewrite, ssl, actions, and include (plus dav, dav_fs, and auth_digest if you want to use WebDAV):
a2enmod suexec rewrite ssl actions include a2enmod dav_fs dav auth_digest
Restart Apache afterwards:
/etc/init.d/apache2 restart
10.Install PureFTPd And Quota[править]
PureFTPd and quota can be installed with the following command:
apt-get install pure-ftpd-common pure-ftpd-mysql quota quotatool
Edit the file /etc/default/pure-ftpd-common...
vi /etc/default/pure-ftpd-common
... and make sure the start mode is set to standalone and set VIRTUALCHROOT=true:
[...] STANDALONE_OR_INETD=standalone [...] VIRTUALCHROOT=true [...]
Edit the file /etc/inetd.conf to prevent inetd from trying to start ftp:
vi /etc/inetd.conf
If there is a line beginning withftp stream tcp, comment it out (if there's no such file, then that is fine, and you don't have to modify /etc/inetd.conf):
[...] #:STANDARD: These are standard services. #ftp stream tcp nowait root /usr/sbin/tcpd /usr/sbin/pure-ftpd-wrapper [...]
If you had to modify /etc/inetd.conf, restart inetd now:
/etc/init.d/openbsd-inetd restart
Now we configure PureFTPd to allow FTP and TLS sessions. FTP is a very insecure protocol because all passwords and all data are transferred in clear text. By using TLS, the whole communication can be encrypted, thus making FTP much more secure.
If you want to allow FTP and TLS sessions, run
echo 1 > /etc/pure-ftpd/conf/TLS
In order to use TLS, we must create an SSL certificate. I create it in /etc/ssl/private/, therefore I create that directory first:
mkdir -p /etc/ssl/private/
Afterwards, we can generate the SSL certificate as follows:
openssl req -x509 -nodes -days 7300 -newkey rsa:2048 -keyout /etc/ssl/private/ pure-ftpd.pem -out /etc/ssl/private/pure-ftpd.pem
Country Name (2 letter code) [AU]: <-- Enter your Country Name (e.g., "DE"). State or Province Name (full name) [Some-State]: <-- Enter your State or Province Name. Locality Name (eg, city) []: <-- Enter your City. Organization Name (eg, company) [Internet Widgits Pty Ltd]: <-- Enter your Organization Name (e.g., the name of your company). Organizational Unit Name (eg, section) []: <-- Enter your Organizational Unit Name (e.g. "IT Department"). Common Name (eg, YOUR name) []: <-- Enter the Fully Qualified Domain Name of the system (e.g. "server1.example.com"). Email Address []: <-- Enter your Email Address.
Change the permissions of the SSL certificate:
chmod 600 /etc/ssl/private/pure-ftpd.pem
Then restart PureFTPd:
/etc/init.d/pure-ftpd-mysql restart
Edit /etc/fstab. Mine looks like this (I added ,usrjquota=aquota.user,grpjquota=aquota.group,jqfmt=vfsv0 to the partition with the mount point /):
vi /etc/fstab
# /etc/fstab: static file system information. # # Use 'blkid' to print the universally unique identifier for a # device; this may be used with UUID= as a more robust way to name devices # that works even if disks are added and removed. See fstab(5). # # <file system> <mount point> <type> <options> <dump> <pass> proc /proc proc defaults 0 0 # / was on /dev/sda1 during installation UUID=92bceda2-5ae4-4e3a-8748-b14da48fb297 / ext3 errors=remount- ro,usrjquota=aquota.user,grpjquota=aquota.group,jqfmt=vfsv0 0 1 # swap was on /dev/sda5 during installation UUID=e24b3e9e-095c-4b49-af27-6363a4b7d094 none swap sw 0 0 /dev/scd0 /media/cdrom0 udf,iso9660 user,noauto 0 0 /dev/fd0 /media/floppy0 auto rw,user,noauto 0 0
To enable quota, run these commands:
mount -o remount / quotacheck -avugm quotaon -avug
11. Install BIND DNS Server[править]
BIND can be installed as follows:
apt-get install bind9 dnsutils
12. Install Vlogger, Webalizer, And AWstats[править]
Vlogger, webalizer, and AWstats can be installed as follows:
apt-get install vlogger webalizer awstats geoip-database
Open /etc/cron.d/awstats afterwards...
vi /etc/cron.d/awstats
... and comment out both cron jobs in that file:
#*/10 * * * * www-data [ -x /usr/share/awstats/tools/update.sh ] && /usr/share/awstats/tools/update.sh # Generate static reports: #10 03 * * * www-data [ -x /usr/share/awstats/tools/buildstatic.sh ] && /usr/share/awstats/tools/buildstatic.sh
13. Install Jailkit[править]
Jailkit is needed only if you want to chroot SSH users. It can be installed as follows (important: Jailkit must be installed before ISPConfig - it cannot be installed afterwards!):
apt-get install build-essential autoconf automake1.9 libtool flex bison debhelper
cd /tmp wget http://olivier.sessink.nl/jailkit/jailkit-2.14.tar.gz tar xvfz jailkit-2.14.tar.gz cd jailkit-2.14 ./debian/rules binary cd .. dpkg -i jailkit_2.14-1_*.deb rm -rf jailkit-2.14*
14. Install fail2ban[править]
This is optional but recommended, because the ISPConfig monitor tries to show the log:
apt-get install fail2ban
To make fail2ban monitor PureFTPd and Dovecot, create the file /etc/fail2ban/jail.local:
vi /etc/fail2ban/jail.local
[pureftpd] enabled = true port = ftp filter = pureftpd logpath = /var/log/syslog maxretry = 3 [dovecot-pop3imap] enabled = true filter = dovecot-pop3imap action = iptables-multiport[name=dovecot-pop3imap, port="pop3,pop3s,imap,imaps", protocol=tcp] logpath = /var/log/mail.log maxretry = 5
Then create the following two filter files:
vi /etc/fail2ban/filter.d/pureftpd.conf
[Definition] failregex = .*pure-ftpd: \(.*@<HOST>\) \[WARNING\] Authentication failed for user.* ignoreregex = vi /etc/fail2ban/filter.d/dovecot-pop3imap.conf
[Definition] failregex = (?: pop3-login|imap-login): .*(?:Authentication failure|Aborted login \(auth failed| Aborted login \(tried to use disabled|Disconnected \(auth failed|Aborted login \ (\d+ authentication attempts).*rip=(?P<host>\S*),.* ignoreregex =
Restart fail2ban afterwards:
/etc/init.d/fail2ban restart
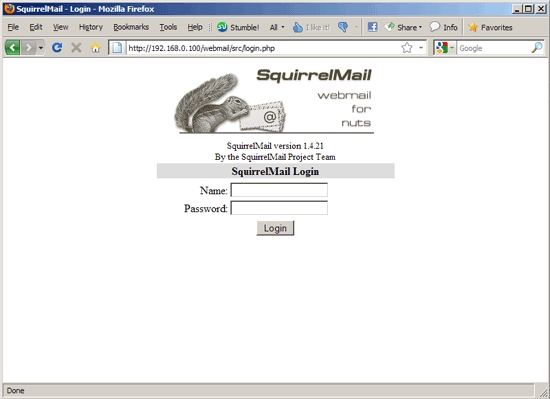
15. Install SquirrelMail[править]
To install the SquirrelMail webmail client, run
apt-get install squirrelmail
Then create the following symlink...
ln -s /usr/share/squirrelmail/ /var/www/webmail
... and configure SquirrelMail:
squirrelmail-configure
We must tell SquirrelMail that we are using Dovecot-IMAP/-POP3:
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. Themes
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Languages
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> <-- D
SquirrelMail Configuration : Read: config.php
---------------------------------------------------------
While we have been building SquirrelMail, we have discovered some
preferences that work better with some servers that don't work so
well with others. If you select your IMAP server, this option will
set some pre-defined settings for that server.
Please note that you will still need to go through and make sure
everything is correct. This does not change everything. There are
only a few settings that this will change.
Please select your IMAP server:
bincimap = Binc IMAP server
courier = Courier IMAP server
cyrus = Cyrus IMAP server
dovecot = Dovecot Secure IMAP server
exchange = Microsoft Exchange IMAP server
hmailserver = hMailServer
macosx = Mac OS X Mailserver
mercury32 = Mercury/32
uw = University of Washington's IMAP server
gmail = IMAP access to Google mail (Gmail) accounts
quit = Do not change anything
Command >> <-- dovecot
SquirrelMail Configuration : Read: config.php
---------------------------------------------------------
While we have been building SquirrelMail, we have discovered some
preferences that work better with some servers that don't work so
well with others. If you select your IMAP server, this option will
set some pre-defined settings for that server.
Please note that you will still need to go through and make sure
everything is correct. This does not change everything. There are
only a few settings that this will change.
Please select your IMAP server:
bincimap = Binc IMAP server
courier = Courier IMAP server
cyrus = Cyrus IMAP server
dovecot = Dovecot Secure IMAP server
exchange = Microsoft Exchange IMAP server
hmailserver = hMailServer
macosx = Mac OS X Mailserver
mercury32 = Mercury/32
uw = University of Washington's IMAP server
gmail = IMAP access to Google mail (Gmail) accounts
quit = Do not change anything
Command >> dovecot
imap_server_type = dovecot
default_folder_prefix = <none>
trash_folder = Trash
sent_folder = Sent
draft_folder = Drafts
show_prefix_option = false
default_sub_of_inbox = false
show_contain_subfolders_option = false
optional_delimiter = detect
delete_folder = false
Press any key to continue... <-- press a key
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. Themes
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Languages
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> <-- S
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. Themes
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Languages
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> <-- Q
Afterwards you can access SquirrelMail under http://server1.example.com/webmail or http://192.168.0.100/webmail:
16. Install ISPConfig 3[править]
To install ISPConfig 3 from the latest released version, do this:
cd /tmp wget http://www.ispconfig.org/downloads/ISPConfig-3-stable.tar.gz tar xfz ISPConfig-3-stable.tar.gz cd ispconfig3_install/install/
The next step is to run
php -q install.php
This will start the ISPConfig 3 installer. The installer will configure all services like Postfix, Dovecot, etc. for you. A manual setup as required for ISPConfig 2 (perfect setup guides) is not necessary.
root@server1:/tmp/ispconfig3_install/install# php -q install.php
>> Initial configuration
Operating System: Debian 6.0 (Squeeze/Sid) or compatible
Following will be a few questions for primary configuration so be careful. Default values are in [brackets] and can be accepted with <ENTER>. Tap in "quit" (without the quotes) to stop the installer.
Select language (en,de) [en]: <-- ENTER
Installation mode (standard,expert) [standard]: <-- ENTER
Full qualified hostname (FQDN) of the server, eg server1.domain.tld [server1.example.com]: <-- ENTER
MySQL server hostname [localhost]: <-- ENTER
MySQL root username [root]: <-- ENTER
MySQL root password []: <-- yourrootsqlpassword
MySQL database to create [dbispconfig]: <-- ENTER
MySQL charset [utf8]: <-- ENTER
Generating a 2048 bit RSA private key
....+++
............................+++
writing new private key to 'smtpd.key'
You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank.
Country Name (2 letter code) [AU]: <-- ENTER State or Province Name (full name) [Some-State]: <-- ENTER Locality Name (eg, city) []: <-- ENTER Organization Name (eg, company) [Internet Widgits Pty Ltd]: <-- ENTER Organizational Unit Name (eg, section) []: <-- ENTER Common Name (eg, YOUR name) []: <-- ENTER Email Address []: <-- ENTER Configuring Jailkit Configuring Dovecot Configuring Spamassassin Configuring Amavisd Configuring Getmail Configuring Pureftpd Configuring BIND Configuring Apache Configuring Vlogger Configuring Apps vhost Configuring Firewall Installing ISPConfig ISPConfig Port [8080]: <-- ENTER Configuring DBServer Installing ISPConfig crontab no crontab for root no crontab for getmail Restarting services ... Stopping MySQL database server: mysqld. Starting MySQL database server: mysqld. Checking for corrupt, not cleanly closed and upgrade needing tables.. Stopping Postfix Mail Transport Agent: postfix. Starting Postfix Mail Transport Agent: postfix. Stopping amavisd: amavisd-new. Starting amavisd: amavisd-new. Stopping ClamAV daemon: clamd. Starting ClamAV daemon: clamd Bytecode: Security mode set to "TrustSigned". . If you have trouble with authentication failures, enable auth_debug setting. See http://wiki.dovecot.org/WhyDoesItNotWork This message goes away after the first successful login. Restarting IMAP/POP3 mail server: dovecot. Restarting web server: apache2 ... waiting .. Restarting ftp server: Running: /usr/sbin/pure-ftpd-mysql-virtualchroot -l mysql:/etc/pure-ftpd/db/mysql.conf -l pam -Y 1 -8 UTF-8 -H -D -b -O clf:/var/log/ pure-ftpd/transfer.log -E -u 1000 -A -B Installation completed. root@server1:/tmp/ispconfig3_install/install#
The installer automatically configures all underlying services, so no manual configuration is needed.
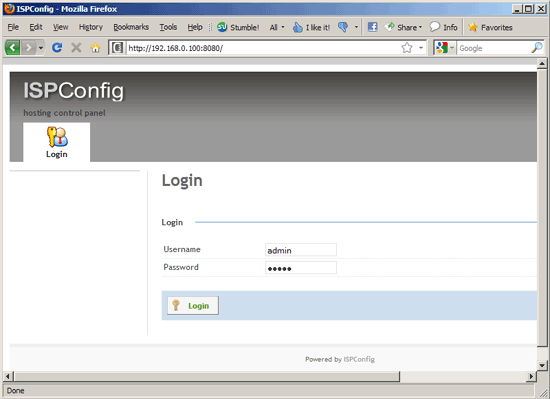
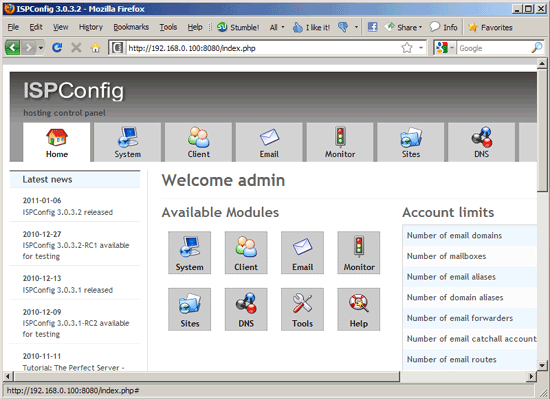
Afterwards you can access ISPConfig 3 under http://server1.example.com:8080/ or http://192.168.0.100:8080/. Log in with the username admin and the password admin (you should change the default password after your first login):
The system is now ready to be used.
16.1 ISPConfig 3 Manual[править]
In order to learn how to use ISPConfig 3, I strongly recommend to download the ISPConfig 3 Manual.
On about 300 pages, it covers the concept behind ISPConfig (admin, resellers, clients), explains how to install and update ISPConfig 3, includes a reference for all forms and form fields in ISPConfig together with examples of valid inputs, and provides tutorials for the most common tasks in ISPConfig 3. It also lines out how to make your server more secure and comes with a troubleshooting section at the end.
16.2 ISPConfig Monitor App For Android[править]
With the ISPConfig Monitor App, you can check your server status and find out if all services are running as expected. You can check TCP and UDP ports and ping your servers. In addition to that you can use this app to request details from servers that have ISPConfig installed (please note that the minimum installed ISPConfig 3 version with support for the ISPConfig Monitor App is 3.0.3.3!); these details include everything you know from the Monitor module in the ISPConfig Control Panel (e.g. services, mail and system logs, mail queue, CPU and memory info, disk usage, quota, OS details, RKHunter log, etc.), and of course, as ISPConfig is multiserver-capable, you can check all servers that are controlled from your ISPConfig master server.
For download and usage instructions, please visit http://www.ispconfig.org/ispconfig-3/ispconfig-monitor-app-for-android/.
17. Additional Notes[править]
17.1 OpenVZ[править]
If the Debian server that you've just set up in this tutorial is an OpenVZ container (virtual machine), you should do this on the host system (I'm assuming that the ID of the OpenVZ container is 101 - replace it with the correct VPSID on your system):
VPSID=101
for CAP in CHOWN DAC_READ_SEARCH SETGID SETUID NET_BIND_SERVICE NET_ADMIN
SYS_CHROOT SYS_NICE CHOWN DAC_READ_SEARCH SETGID SETUID NET_BIND_SERVICE NET_
ADMIN SYS_CHROOT SYS_NICE
do
vzctl set $VPSID --capability ${CAP}:on --save
done
17.2 SquirrelMail[править]
Lots of people have reported problems (such as getting 404 Not Found errors) using the SquirrelMail webmail package in their web sites created through ISPConfig 3. This guide explains how to configure SquirrelMail on a Debian Squeeze server so that you can use it from within your web sites (created through ISPConfig).
SquirrelMail's Apache configuration is in the file /etc/squirrelmail/apache.conf, but this file isn't loaded by Apache because it is not in the /etc/apache2/conf.d/ directory. Therefore we create a symlink called squirrelmail.conf in the /etc/apache2/conf.d/ directory that points to /etc/squirrelmail/apache.conf and reload Apache afterwards:
cd /etc/apache2/conf.d/ ln -s ../../squirrelmail/apache.conf squirrelmail.conf /etc/init.d/apache2 reload
Now open /etc/apache2/conf.d/squirrelmail.conf...
vi /etc/apache2/conf.d/squirrelmail.conf
... and add the following lines to the <Directory /usr/share/squirrelmail></Directory> container that make sure that mod_php is used for accessing SquirrelMail, regardless of what PHP mode you select for your website in ISPConfig:
[...]
<Directory /usr/share/squirrelmail>
Options FollowSymLinks
<IfModule mod_php5.c>
AddType application/x-httpd-php .php
php_flag magic_quotes_gpc Off
php_flag track_vars On
php_admin_flag allow_url_fopen Off
php_value include_path .
php_admin_value upload_tmp_dir /var/lib/squirrelmail/tmp
php_admin_value open_basedir /usr/share/squirrelmail:/etc/squirrelmail:
/var/lib/squirrelmail:/etc/hostname:/etc/mailname:/var/spool/squirrelmail
php_flag register_globals off
</IfModule>
<IfModule mod_dir.c>
DirectoryIndex index.php
</IfModule>
# access to configtest is limited by default to prevent information leak
<Files configtest.php>
order deny,allow
deny from all
allow from 127.0.0.1
</Files>
</Directory>
[...]
Create the directory /var/lib/squirrelmail/tmp...
mkdir /var/lib/squirrelmail/tmp
... and make it owned by the user www-data:
chown www-data /var/lib/squirrelmail/tmp
Reload Apache again:
/etc/init.d/apache2 reload
That's it already - /etc/apache2/conf.d/squirrelmail.conf defines an alias called /squirrelmail that points to SquirrelMail's installation directory /usr/share/squirrelmail.
You can now access SquirrelMail from your web site as follows:
http://www.example.com/squirrelmail
You can also access it from the ISPConfig control panel vhost as follows (this doesn't need any configuration in ISPConfig):
http://server1.example.com:8080/squirrelmail
If you'd like to use the alias /webmail instead of /squirrelmail, simply open /etc/apache2/conf.d/squirrelmail.conf...
vi /etc/apache2/conf.d/squirrelmail.conf
... and add the line Alias /webmail /usr/share/squirrelmail:
Alias /squirrelmail /usr/share/squirrelmail Alias /webmail /usr/share/squirrelmail [...]
Then reload Apache:
/etc/init.d/apache2 reload
Now you can access Squirrelmail as follows:
http://www.example.com/webmail http://server1.example.com:8080/webmail
If you'd like to define a vhost like webmail.example.com where your users can access SquirrelMail, you'd have to add the following vhost configuration to /etc/apache2/conf.d/squirrelmail.conf:
vi /etc/apache2/conf.d/squirrelmail.conf
[...] <VirtualHost 1.2.3.4:80> DocumentRoot /usr/share/squirrelmail ServerName webmail.example.com </VirtualHost>
Make sure you replace 1.2.3.4 with the correct IP address of your server. Of course, there must be a DNS record for webmail.example.com that points to the IP address that you use in the vhost configuration. Also make sure that the vhost webmail.example.com does not exist in ISPConfig (otherwise both vhosts will interfere with each other!).
Now reload Apache...
/etc/init.d/apache2 reload
... and you can access SquirrelMail under http://webmail.example.com!
18. Links[править]
Debian: http://www.debian.org/
ISPConfig: http://www.ispconfig.org/